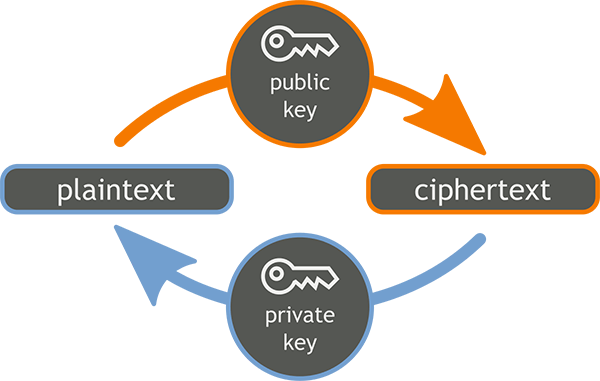
Encrypted Data is Secure Today. But Will it be Crackable with Quantum Computers? Not all encryption will be readily crackable with quantum computers. “Symmetric encryption can be decrypted using the same key that was used to encrypt it, while asymmetric encryption requires one key (the public key) to encrypt and another key (the private key) to decrypt.” But asymmetric encryption which most data is secured with, today, predominantly in communications, is a problem if quantum computers come to fruition as anticipated.
mte. Extract and Graphic: The short answer is yes: encryption can be cracked. A brute force approach, which basically involves making lots and lots of guesses until one turns out to be right, would certainly find the right answer, given enough time and computing power. Given our current capabilities, brute-forcing AES-256 could take up to 3 sexdecillion (3×1051) years, and similar numbers could be attached to many widely-used encryption algorithms. In the future quantum computers and other advances could significantly decrease how secure encryption actually is, but in the meantime it’s effectively impenetrable.
But that doesn’t make encryption foolproof. Attackers are well aware that encrypted data is useless without keys, so what do they go after? The keys. The most catastrophic possible data breach is one in which the encrypted data and the decryption keys are stolen. If data security is being implemented correctly, the keys (multiple keys for different data, probably per user) will be securely stored in a separate location from the data and should probably be encrypted themselves. Additionally, the keys will need to be securely decrypted and fetched every time some data needs to be decrypted, so that attackers can’t intercept it. On top of all that, the keys should probably be changed on a regular basis.
Full discussion is found at mte…